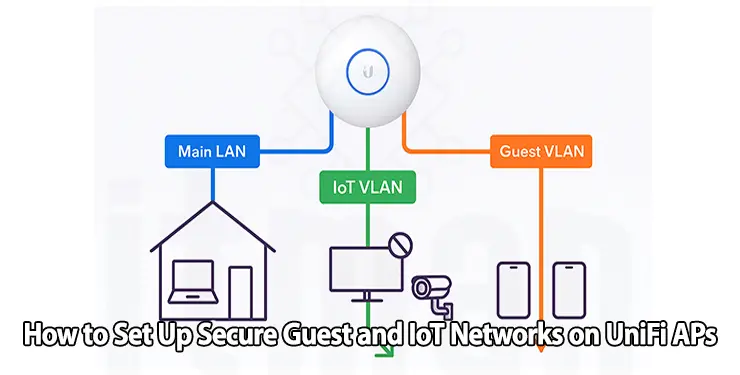
In modern home and office environments, security is everything. With more devices than ever—smart TVs, thermostats, IP cameras, and guest smartphones—network segmentation has gone from a “nice-to-have” to an absolute necessity. Setting up secure guest and IoT networks using UniFi Access Points allows you to isolate potentially vulnerable devices from your main network. This not only protects your private data but also ensures better network performance and control.
Whether you’re a small business owner or a tech-savvy homeowner, this guide will walk you through everything you need to know—step-by-step.
Step 1: Understand VLANs and Why They Matter
Before jumping into the UniFi dashboard, it’s important to understand VLANs (Virtual Local Area Networks).
A VLAN allows you to separate traffic at the Layer 2 level. With UniFi, VLANs are essential for isolating traffic between your main LAN, guest users, and IoT devices.
For example:
- VLAN 10 → Main LAN (your personal devices)
- VLAN 20 → Guest network
- VLAN 30 → IoT network
This separation is the backbone of building secure guest and IoT networks.
Step 2: Create VLANs in UniFi Network Controller
Let’s begin with the VLAN setup:
- Log into your UniFi Network Controller.
- Navigate to Settings > Networks.
- Click Create New Network.
- Set the following:
- Name: Guest_Network / IoT_Network
- Purpose: Corporate
- VLAN ID: Use something unique (e.g., 20 for guest, 30 for IoT)
- Gateway/Subnet: Assign a subnet (e.g., 192.168.20.1/24 for guests)
- Enable DHCP or define static IP if needed.
Repeat the process for each segment you want to isolate. This creates logical barriers between your secure guest network and the IoT devices.
Step 3: Assign SSIDs to Each Network
Now that your VLANs are ready, let’s map them to Wi-Fi SSIDs:
- Go to Settings > Wi-Fi.
- Click Add New Wi-Fi Network.
- Set:
- SSID: Something clear like “Guest_WiFi” or “IoT_Devices”
- Network: Select the VLAN you created earlier (e.g., Guest_Network → VLAN 20)
- Security Protocol: WPA2/WPA3 Personal (unless open for guests)
- Guest Policies: Enable if this is the guest network
- Disable “Broadcast SSID” for IoT if you want added obscurity.
This ensures that traffic from these SSIDs is routed according to VLAN policies, helping you build secure guest and IoT networks effortlessly.
Step 4: Set Up Firewall Rules for Isolation and Security
VLANs without firewall rules are only half the battle. Next, we need to restrict what each network can access:
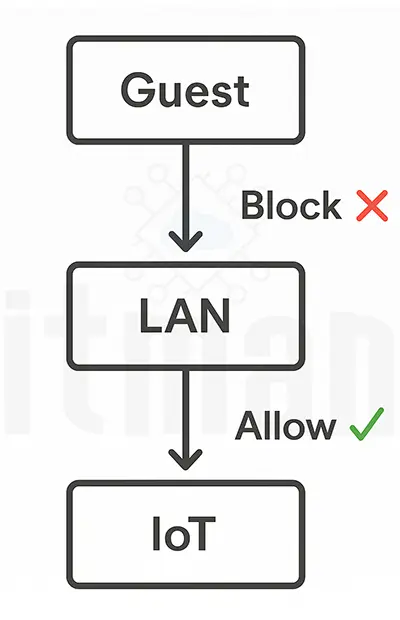
A. Restrict Guests from Accessing Internal Network
- Go to Settings > Firewall & Security > Rules > LAN IN.
- Create a new rule:
- Action: Drop
- Source: Guest VLAN (e.g., 192.168.20.0/24)
- Destination: LAN (192.168.1.0/24)
- Description: Block Guest to LAN
- Enabled: Yes
This isolates secure guest traffic from your personal LAN.
B. Block IoT Devices from Initiating Outbound LAN Traffic
IoT devices are often poorly secured. Limiting their access is key:
- Create a second rule:
- Action: Drop
- Source: IoT VLAN (192.168.30.0/24)
- Destination: LAN (192.168.1.0/24)
- Description: Block IoT to LAN
To allow LAN to access IoT (like accessing your IP camera from phone), create an allow rule:
- Source: LAN
- Destination: IoT VLAN
- Action: Accept
With these rules, your IoT network stays isolated but manageable.
Step 5: Enable Guest Control (Captive Portal, Rate Limits)
For secure guest networks, UniFi offers a “Guest Control” section that adds useful restrictions:
- Go to Settings > Guest Control.
- Enable:
- Guest Portal (optional login page)
- Access Expiration (to kick off devices after 1–2 hours)
- Bandwidth Limits (avoid hogging)
- Restricted Subnets: Block access to known internal networks
Captive portals are great for office environments or cafes. Even at home, these tools help maintain a secure guest experience.
Step 6: Apply Device Isolation for Guests and IoT
You can also use client isolation features in UniFi:
- For guests, enable “Guest Policies > Access Restrictions > Isolate Guests.”
- For IoT, go to the Wi-Fi settings and toggle on “Client Device Isolation.”
This ensures devices in the same VLAN or SSID can’t even talk to each other—a big plus for secure IoT networks.
Step 7: Testing Your Configuration
Once everything is set up, it’s crucial to verify your segmentation:
- Connect to the guest SSID → Try pinging your personal laptop → Should fail.
- Connect to IoT → Try accessing the router interface → Should fail.
- Try connecting from LAN to an IoT device (e.g., IP camera) → Should work.
- Try using the captive portal as a guest.
These tests ensure your secure guest and IoT networks are functioning as intended.
Step 8: Monitor and Maintain Your Segmented Networks
Setting it up is one thing—keeping it secure is another.
- Use UniFi Insights > Clients to monitor who is connected and where.
- Regularly audit firewall rules and SSID usage.
- Change Wi-Fi passwords for guest networks often.
- Consider placing IoT devices that require internet access on a separate VLAN with limited DNS/DHCP to reduce tracking or data exfiltration.
Final Thoughts: Why This Setup Matters
In today’s connected environments, building secure guest and IoT networks isn’t optional—it’s foundational. With UniFi APs and the built-in VLAN and firewall capabilities, even non-enterprise users can segment traffic, protect their data, and manage devices with confidence. Whether you’re guarding business-critical systems or just protecting your Netflix stream from rogue smart plugs, this approach ensures peace of mind.
Frequently Asked Questions (FAQ)
1. Why should I separate my guest and IoT networks from the main LAN?
Separating guests and IoT devices from your primary LAN helps reduce security risks. Guest devices can be unknown and potentially unsafe, while many IoT devices lack proper security updates. Isolating them ensures your secure guest and IoT networks don’t become entry points to your main network.
2. Can UniFi handle multiple VLANs and SSIDs easily?
Yes! UniFi Access Points and their controller platform are built with VLAN support in mind. You can assign different VLANs to different SSIDs and apply firewall rules to manage access, creating truly secure guest and IoT networks.
3. Is setting up VLANs on UniFi complicated for beginners?
Not at all. While VLANs may sound technical, UniFi makes the process user-friendly through its web interface. With just a few steps, you can assign VLANs to SSIDs and apply access rules—even if you’re not a network engineer.
4. Do I need a UniFi Security Gateway (USG) or Dream Machine for VLAN support?
Yes, to fully implement VLAN segmentation and firewall rules, you’ll need a UniFi router that supports Layer 3 functionality—like the UniFi Dream Machine, Dream Router, or UniFi Security Gateway. Without these, VLANs won’t route properly across your network.
5. Can I use the same SSID for both guest and IoT networks?
Technically, no. Each VLAN should have its own SSID for clarity and control. Sharing SSIDs across VLANs is not supported and would defeat the purpose of segmentation. Separate SSIDs help enforce access policies and strengthen your secure guest and IoT networks.
6. How do I allow my phone (on the main LAN) to access an IoT camera on another VLAN?
You can create a specific firewall rule that allows traffic from your LAN (e.g., 192.168.1.0/24) to the IP of your camera on the IoT VLAN (e.g., 192.168.30.10). Keep all other traffic from IoT VLAN to LAN blocked to maintain isolation.
7. What’s the best way to keep guest users from abusing bandwidth?
Enable guest control features in UniFi:
- Use bandwidth limits
- Set access expiration times
- Optionally use captive portal for terms and conditions
These tools help ensure a smooth and fair experience for all users on your secure guest network.
8. How often should I update firewall rules or review network access?
It’s a good idea to:
- Review firewall rules every 3–6 months
- Monitor connected devices weekly via UniFi’s “Clients” section
- Reassess VLAN needs if new devices or users are added
Ongoing review ensures your IoT networks and guest access stay secure over time.
9. Can I hide the IoT SSID for better security?
Absolutely. Hiding the SSID (by disabling “Broadcast SSID”) makes it less visible to casual users. Combine this with MAC filtering or pre-shared keys for a more locked-down IoT network setup.
10. Will segmenting networks slow down my Wi-Fi performance?
Not at all. In fact, proper segmentation can improve overall performance by reducing unnecessary broadcast traffic. It also allows better traffic shaping and QoS settings across secure guest and IoT networks.